Menu
close
A hypervisor is a type of software that allows multiple operating systems to run on a single physical computer.
The concept of virtualisation serves as the cornerstone for modern technology. It allows for the creation of virtual environments that mimic physical systems, providing a more efficient and flexible approach to computing. With virtualisation, resources can be shared and managed in a centralised manner, leading to increased scalability and cost savings.
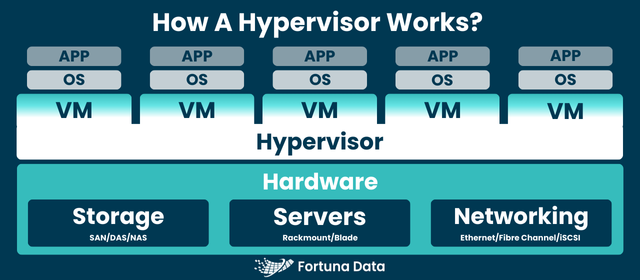
A hypervisor, also known as a virtual machine monitor (VMM), is a specialised software layer that allows one physical host machine to support multiple distinct virtual machines (VMs). This means that instead of having one operating system on dedicated hardware, the hypervisor distributes and manages the available resources - processing, memory, storage, and networking - among several independent computing environments.
In short, the hypervisor enables the virtualisation of hardware, providing IT environments with increased efficiency, flexibility, and scalability. This feature serves as the foundation for various contemporary computing approaches, including server consolidation, cloud computing, desktop virtualisation, and agile development processes.
In the standard process, computers typically run one operating system that oversees both hardware functions and user programs. However, a hypervisor alters this approach by implementing an intermediate layer between the physical hardware and the operating systems. This is achieved through advanced management techniques.
In the case of a VM making a request for an instruction or resource, the hypervisor acts as a mediator and communicates with the physical hardware accordingly. It also manages the status and needs of all VMs, promoting equitable allocation and avoiding contention over resources.
Hypervisors can be divided into two primary categories: Type 1, also known as bare-metal hypervisors, and Type 2, or hosted hypervisors
Type 1 Hypervisors (Bare-Metal)
Bare-metal hypervisors, also known as Type 1 hypervisors, are essential virtualisation tools used for optimising server resources.
Type 1 hypervisors operate directly on the hardware, bypassing the need for a traditional operating system. Positioned as the initial layer above the physical server, they offer superior performance, scalability, and security.
Performance: Type 1 hypervisors can minimise latency and maximise resource utilisation because of their direct interaction with hardware.
Enterprise data centres and cloud providers utilise Type 1 hypervisors for scalability, allowing them to host thousands of VMs.
Security and Isolation: Direct resource management and hardware partitioning enhance VM isolation and minimise potential attack areas.
Some illustrations of Type 1 hypervisors include...
Usual scenarios include those in enterprise information technology, extensive cloud infrastructure, and virtualised data centres.
Type 2 Hypervisors (Hosted)
Hosted Type 2 Hypervisors refer to virtualisation software that runs on top of a host operating system, as opposed to being directly installed on physical hardware.
Type 2 hypervisors function as applications on top of an existing operating system, providing virtualisation within a running environment.
Some examples of hypervisors belonging to Type 2 include VMware Workstation, Oracle VM VirtualBox, and Microsoft Hyper-V.
Typical scenarios include development and educational purposes, as well as personal virtualisation requirements.

The two types of hypervisors are Type 1 and Type 2.
Operates on Physical Components and Operating System of Host Device.
The level of performance ranges from high to moderate.
The use case involves various platforms such as enterprise, cloud, server, and desktop, catering to tasks such as testing and development.
"Ensuring security through both strong hardware and operating system-level isolation measures."
Some popular virtualisation software includes ESXi, Hyper-V, and Xen for server use and Workstation and VirtualBox for personal use.
Additional options for Hypervisor models.
The significance of hypervisors lies in their ability to efficiently manage and partition the physical resources of a computer system. They enable multiple operating systems to run simultaneously, maximising the utilisation of hardware and enhancing flexibility in resource allocation. This critical technology plays a crucial role in modern computing environments.
Hypervisors offer significant benefits to both IT infrastructure and management, driving powerful improvements.
Some advantages of this product include its versatility, convenience, and efficiency.
The various scenarios in which something can be utilised and the functions that it entails
The security concerns associated with hypervisors.
Possible hazards:
The implementation details may differ, depending on the architecture being used (Type 1 or Type 2).
When choosing the appropriate hypervisor, there are certain factors that must be considered in order to make the best decision.
When selecting a hypervisor, it is important for organisations to consider:
Type 2 hypervisors may be suitable for small businesses and developers, while Type 1 hypervisors are typically the preferred choice for large enterprises, data centres, and cloud infrastructure due to their strong reliability and high performance.
The outlook for hypervisors is promising, as they continue to play a pivotal role in virtualisation technology.
As IT trends progress, so do hypervisors. Some of the latest developments in this technology include:
Leading technology companies remain committed to enhancing hypervisor performance, intelligence, and user-friendliness, as they prioritise the inclusion of hybrid cloud and multi-cloud orchestration capabilities
In conclusion, it is evident that the results clearly support our initial hypothesis.
Hypervisors are a foundational technology that drives virtualisation, empowering businesses to optimise resource usage, decrease expenses, increase adaptability, and provide dependable and scalable IT solutions. Whether overseeing dynamic desktop setups or robust cloud-based data centres, hypervisors remain integral for advanced computing needs.
Gaining insight into the differences between Type 1 and Type 2 hypervisors, as well as their unique designs and advantages, enables IT experts to make educated choices regarding virtualisation plans. This lays the groundwork for advancements in both corporate and personal computing.
This all-inclusive piece delves into hypervisors, spanning their core function and structure to real-world implications, categories, implementation choices, security factors, and upcoming developments. As a central component of contemporary virtualised and cloud-based IT environments, the hypervisor often operates unnoticed.